Spring Sale Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = simple70
Pass the Fortinet Network Security Expert NSE5_FNC_AD_7.6 Questions and answers with Dumpstech
Exam NSE5_FNC_AD_7.6 Premium Access
View all detail and faqs for the NSE5_FNC_AD_7.6 exam
Refer to the exhibit.
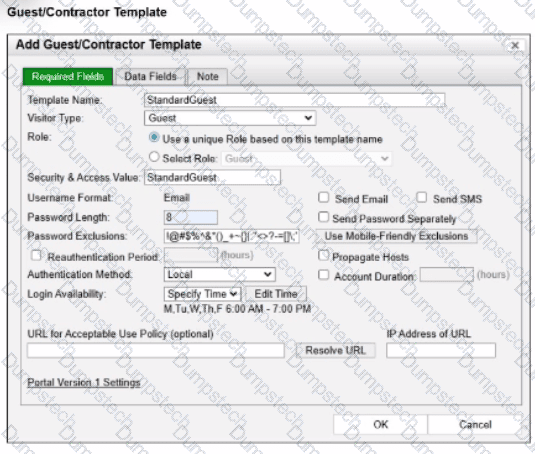
What will happen to the host of a guest user created from this template if the time of connection is 8:00 PM?
A healthcare organization is integrating FortiNAC-F with its existing MDM. Communication is failing between the systems.
What could be a probable cause?
An administrator manages a corporate environment where all users log into the corporate domain each time they connect to the network. The administrator wants to leverage login scripts to use a FortiNAC-F agent to enhance endpoint visibility
Which agent can be deployed as part of a login script?
How can an administrator configure FortiNAC-F to normalize incoming syslog event levels across vendors?
During an evaluation of state-based enforcement, an administrator discovers that ports that should not be under enforcement have been added to enforcement groups.
In which view would the administrator be able to identify who added the ports to the groups?
(Selected)
Where should you configure MAC notification traps on a supported switch?
Refer to the exhibit.
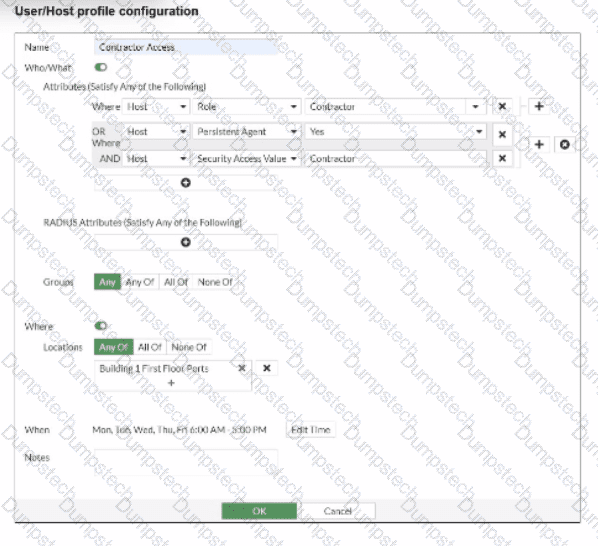
If a host is connected to a port in the Building 1 First Floor Ports group, what must also be true to match this user/host profile?
Which two requirements must be met to set up an N+1 HA cluster? (Choose two.)
When creating a user or host profile, which three criteria can you apply? (Choose three.)
