Spring Sale Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = simple70
Pass the Cisco CyberOps Associate 200-201 Questions and answers with Dumpstech
Which data type is necessary to get information about source/destination ports?
A threat actor penetrated an organization's network. Using the 5-tuple approach, which data points should the analyst use to isolate the compromised host in a grouped set of logs?
An engineer is addressing a connectivity issue between two servers where the remote server is unable to establish a successful session. Initial checks show that the remote server is not receiving an SYN-ACK while establishing a session by sending the first SYN. What is causing this issue?
Which action prevents buffer overflow attacks?
Refer to the exhibit.

Which type of attack is being executed?
Refer to the exhibit.
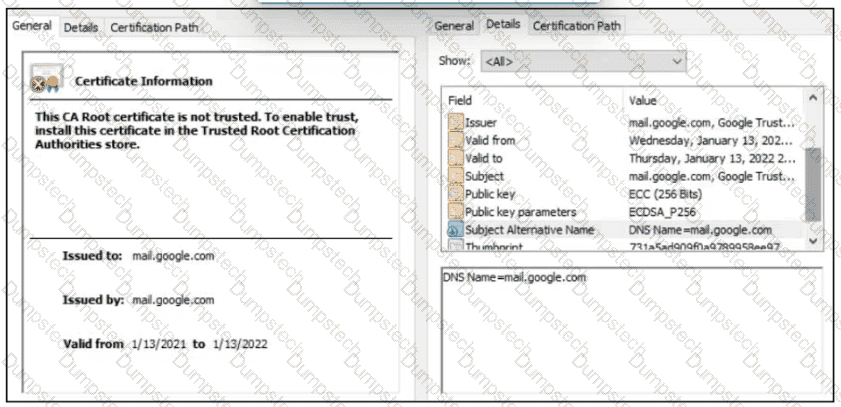
A company employee is connecting to mail google.com from an endpoint device. The website is loaded but with an error. What is occurring?
What is an advantage of symmetric over asymmetric encryption?
What are two social engineering techniques? (Choose two.)
What is a difference between signature-based and behavior-based detection?
Drag and drop the security concept from the left onto the example of that concept on the right.
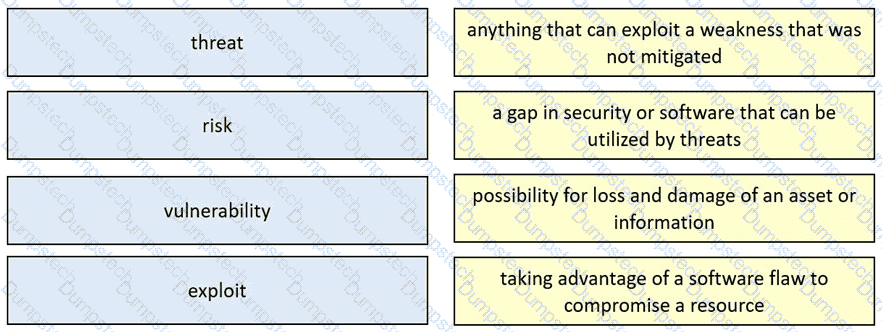

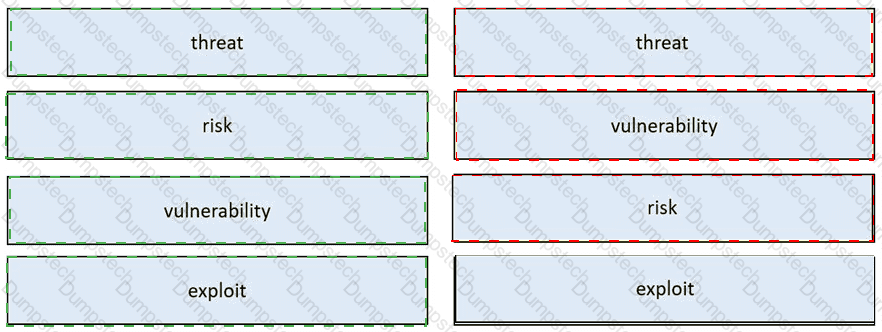
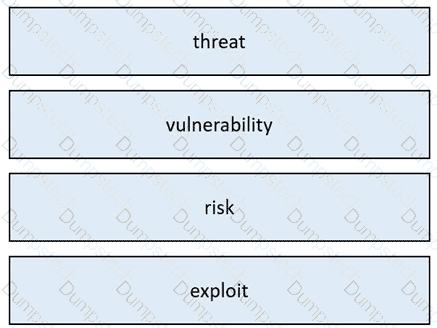 Table Description automatically generated
Table Description automatically generated