Winter Sale Limited Time 65% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = pass65
Pass the Cisco Certified Specialist - Threat Hunting and Defending 300-220 Questions and answers with Dumpstech
Exam 300-220 Premium Access
View all detail and faqs for the 300-220 exam
The security team detects an alert regarding a potentially malicious file namedFinancial_Data_526280622.pdfdownloaded by a user. Upon reviewing SIEM logs and Cisco Secure Endpoint, the team confirms that the file was obtained from an untrusted website. The hash analysis of the file returns an unknown status. Which action must be done next?
During a structured hunt, analysts using Cisco SIEM tools complete hypothesis testing and confirm malicious activity. What is the NEXT step in the Cisco threat hunting lifecycle?
Refer to the exhibit.
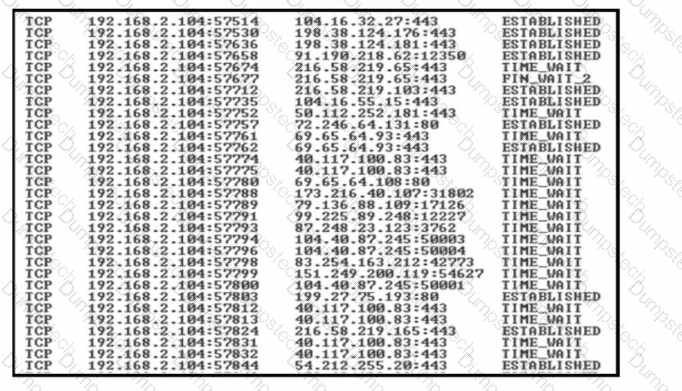
A security team detects a spike in traffic from the company web server. After further investigation, the team discovered that multiple connections have been established from the server to different IP addresses, but the web server logs contain both expected traffic and DDoS traffic. Which attribute must the team use to further filter the logs?
The Security Operations Center team at a company detects a successful VPN connection from a country outside the known countries of operation. After the connection occurs, the team receives multiple triggers from the same source IP address about file access and modifications to the file server. The team concludes that this is a case of data exfiltration from an unknown adversary through a compromised user account. To find other potential actions taken by the adversary, which type of threat hunting should be used?
Refer to the exhibit.
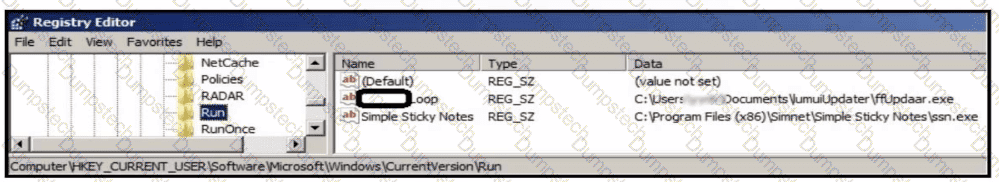
An analyst is evaluating artifacts and logs collected from recent breach. In the logs, ATP established persistency of malware by placing a path to the executable in a specific registry entry. What is the difference between the ATP's approach and using HKEY LOCAL MACHINE\Software\Microsoft\Windows\CurrentVersion\Run instead?
A threat hunting team is attempting to attribute a series of intrusions across multiple organizations to a known threat actor. The malware binaries differ across incidents, infrastructure changes frequently, and IP addresses rotate daily. Which evidence provides the STRONGEST basis for confident attribution?
A threat hunting team wants to ensure hunts are repeatable, scalable, and less dependent on individual analyst intuition. What is the MOST important process improvement?
After completing several successful hunts using Cisco Secure Network Analytics and Secure Endpoint, the SOC wants to ensure long-term defensive improvement. Which action BEST represents a mature threat hunting outcome?
A mature SOC notices that several incidents over the past year involved attackers abusing legitimate administrative tools rather than deploying custom malware. Leadership asks the threat hunting team to improve detection coverage in a way that increases attacker cost rather than relying on easily replaceable indicators. Which detection strategy best aligns with this objective?
What triggers unstructured threat hunting?
