Spring Sale Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = simple70
Pass the Fortinet Certified Professional Network Security FCSS_EFW_AD-7.6 Questions and answers with Dumpstech
Exam FCSS_EFW_AD-7.6 Premium Access
View all detail and faqs for the FCSS_EFW_AD-7.6 exam
Refer to the exhibit, which contains the partial output of an OSPF command.
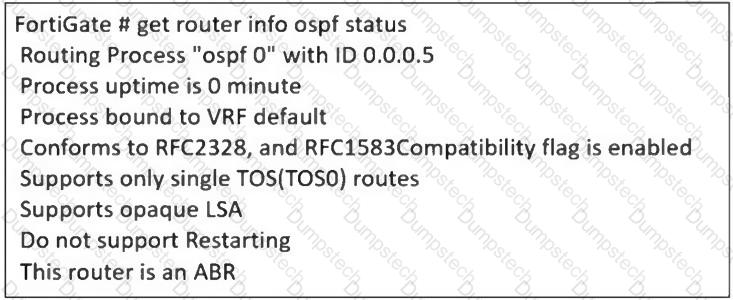
An administrator is checking the OSPF status of a FortiGate device and receives the output shown in the exhibit.
What two conclusions can the administrator draw? (Choose two.)
What is the initial step performed by FortiGate when handling the first packets of a session?
Refer to the exhibit.
A pre-run CLI template that is used in zero-touch provisioning (ZTP) and low-touch provisioning (LTP) with FortiManager is shown.
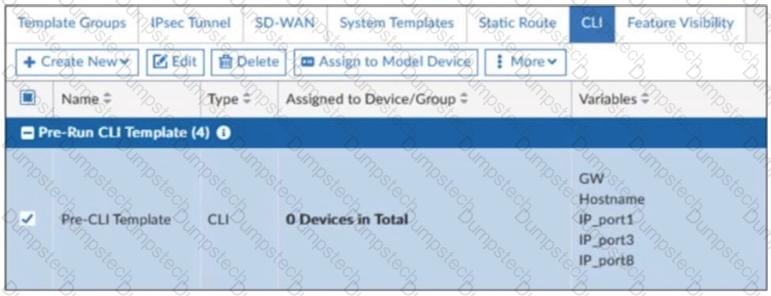
The template is not assigned even though the configuration has already been installed on FortiGate.
What is true about this scenario?
Refer to the exhibit, which shows a corporate network and a new remote office network.
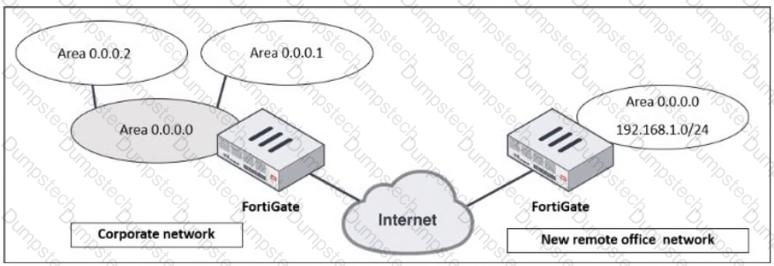
An administrator must integrate the new remote office network with the corporate enterprise network.
What must the administrator do to allow routing between the two networks?
Refer to the exhibit.
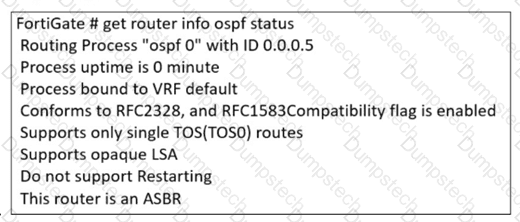
The partial output of an OSPF command is shown. You are checking the OSPF status of a FortiGate device when you receive the output shown in the exhibit. Based on the output, which two statements about FortiGate are correct? (Choose two answers)
Refer to the exhibits.
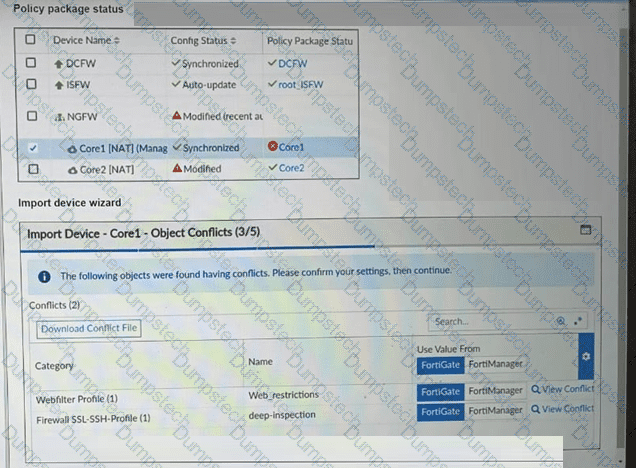
A policy package conflict status and information from the import device wizard in the Core1 VDOM are shown. When you import a policy package, the following message appears for the Web_restrictions web filter profile and the deep-inspection SSL-SSH profile: "The following objects were found having conflicts. Please confirm your settings, then continue." The Web_restrictions and deep-inspection profiles are used by other FortiGate devices within FortiManager. Which step must you take to resolve the issue? (Choose one answer)
Refer to the exhibit, which shows an ADVPN network.
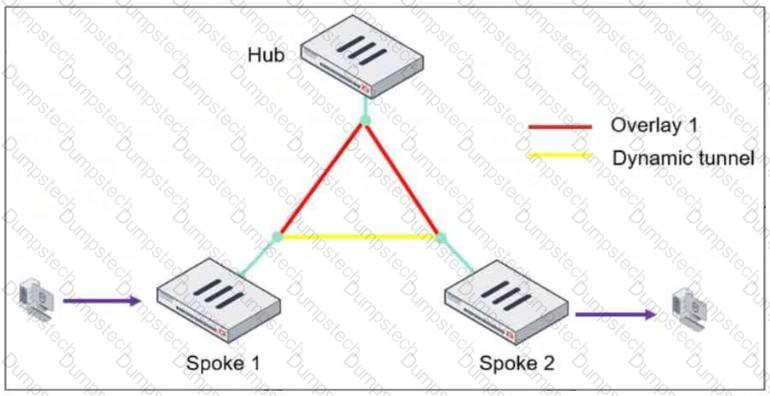
The client behind Spoke-1 generates traffic to the device located behind Spoke-2.
What is the first message that the hub sends to Spoke-1 to bring up the dynamic tunnel?
Refer to the exhibit, which shows the VDOM section of a FortiGate device.
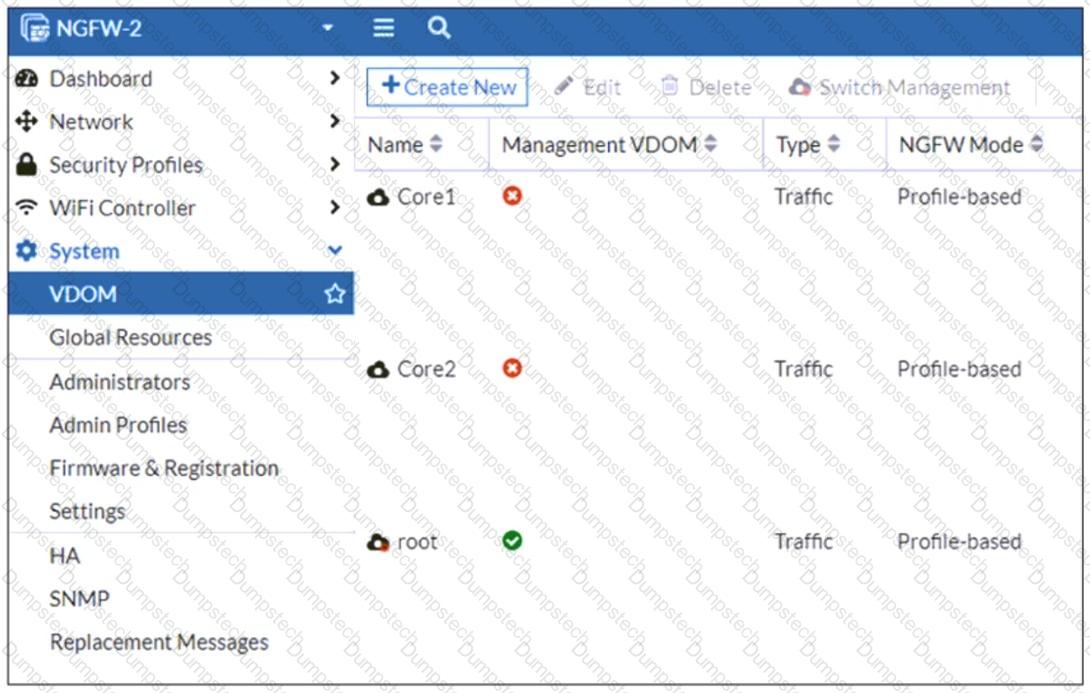
An administrator discovers that webfilter stopped working in Core1 and Core2 after a maintenance window.
Which two reasons could explain why webfilter stopped working? (Choose two.)
Refer to the exhibit, which shows an OSPF network.
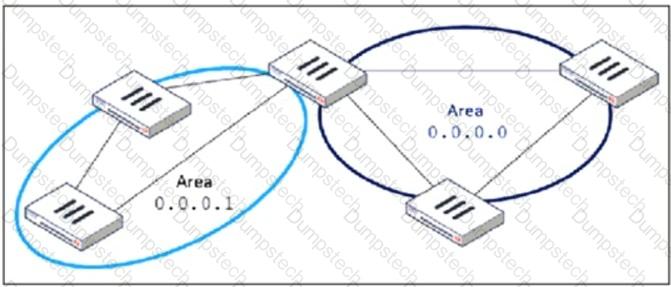
Which configuration must the administrator apply to optimize the OSPF database?
An administrator configured the FortiGate devices in an enterprise network to join the Fortinet Security Fabric. The administrator has a list of IP addresses that must be blocked by the data center firewall. This list is updated daily.
How can the administrator automate a firewall policy with the daily updated list?

 A client behind Spoke-1 sends traffic to a device behind Spoke-2.
A client behind Spoke-1 sends traffic to a device behind Spoke-2. The traffic initially flows through the hub, following the pre-established overlay tunnel.
The traffic initially flows through the hub, following the pre-established overlay tunnel. The hub detects that Spoke-1 is communicating with Spoke-2 and determines that a direct shortcut tunnel between the spokes can optimize the connection.
The hub detects that Spoke-1 is communicating with Spoke-2 and determines that a direct shortcut tunnel between the spokes can optimize the connection. The hub sends a "Shortcut Offer" message to Spoke-1, informing it that a direct dynamic tunnel to Spoke-2 is possible.
The hub sends a "Shortcut Offer" message to Spoke-1, informing it that a direct dynamic tunnel to Spoke-2 is possible. Spoke-1 and Spoke-2 then negotiate and establish a direct IPsec tunnel for communication.
Spoke-1 and Spoke-2 then negotiate and establish a direct IPsec tunnel for communication.