Winter Sale Limited Time 65% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = pass65
Pass the Fortinet Network Security Expert NSE7_SSE_AD-25 Questions and answers with Dumpstech
Exam NSE7_SSE_AD-25 Premium Access
View all detail and faqs for the NSE7_SSE_AD-25 exam
What action must a FortiSASE customer take to restrict organization SaaS access to only FortiSASE-connected users? (Choose one answer)
Which information does FortiSASE use to bring network lockdown into effect on an endpoint? (Choose one answer)
For monitoring potentially unwanted applications on endpoints, which information is available on the FortiSASE software installations page? (Choose two answers)
During FortiSASE provisioning, how many security points of presence (POPs) need to be configured by the FortiSASE administrator?
Refer to the exhibits.
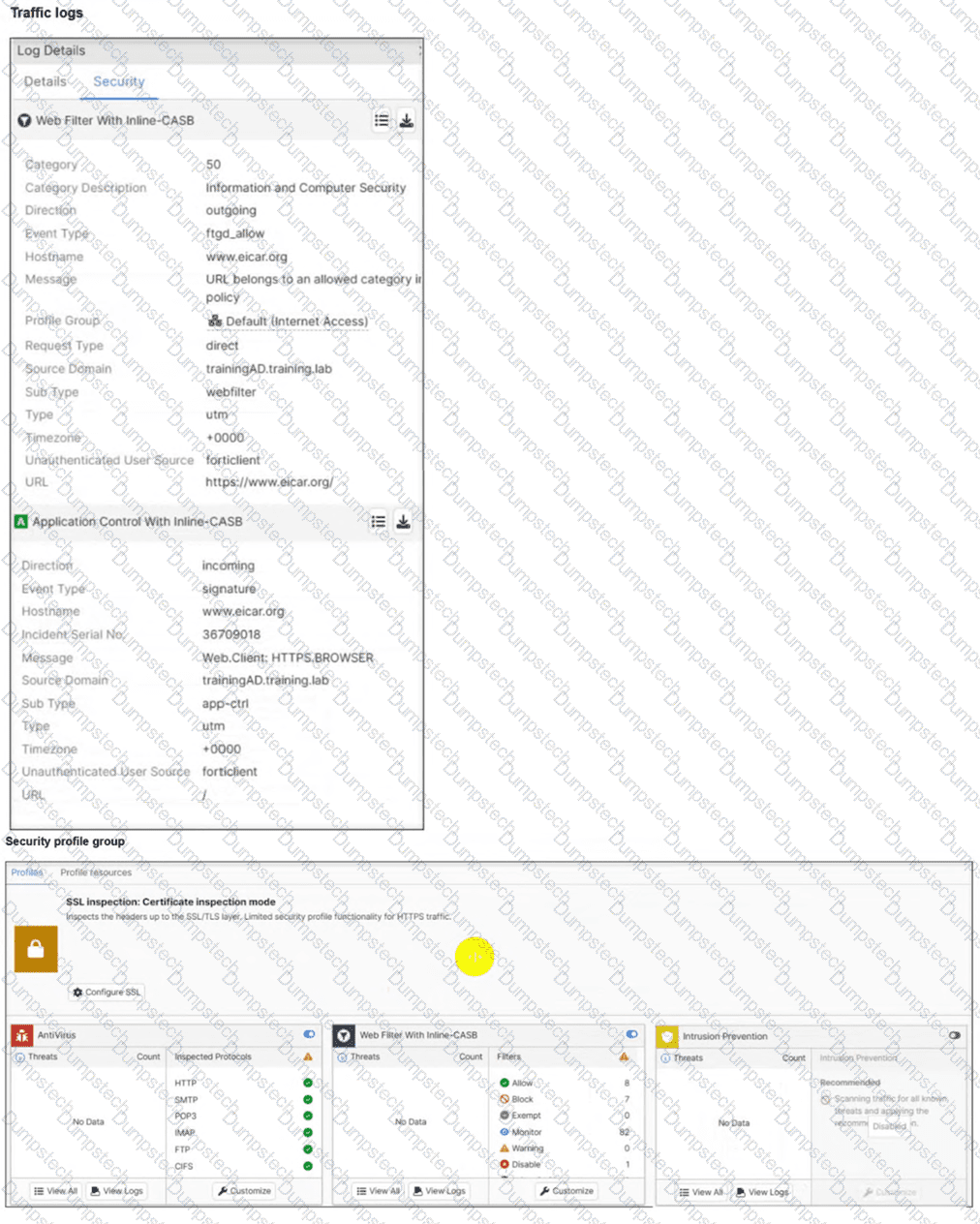
A FortiSASE administrator has configured an antivirus profile in the security profile group and applied it to the internet access policy. Remote users are still able to download the eicar.com-zip file from https://eicar.org.
Which configuration on FortiSASE is allowing users to perform the download? (Choose one answer)
Your FortiSASE customer has a small branch office in which ten users will be using their personal laptops and mobile devices to access the internet. Which deployment should they use to secure their internet access with minimal configuration? (Choose one answer)
A FortiSASE customer has been enforcing always-on VPN for their remote users running FortiClient. What option can be enabled under the customer’s Endpoint Profile to allow them access different resources located in the same L2 network? (Choose one answer)
What are two advantages of using zero-trust tags? (Choose two.)
You are designing a new network, and the cybersecurity policy mandates that all remote users working from home must always be connected and protected. Which FortiSASE component facilitates this always-on security measure? (Choose one answer)
When configuring the DLP rule in FortiSASE using Regex format, what would be the correct order for the configuration steps? (Place the four correct steps in order)


