Spring Sale Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = simple70
Pass the Netskope NCCSA NSK300 Questions and answers with Dumpstech
Exam NSK300 Premium Access
View all detail and faqs for the NSK300 exam
You are implementing a solution to deploy Netskope for machine traffic in an AWS account across multiple VPCs. You want to deploy the least amount of tunnels while providing connectivity for all VPCs.
How would you accomplish this task?
You do not want a scheduled Advanced Analytics dashboard to be automatically updated when Netskope makes improvements to that dashboard. In this scenario, what would you do to retain the original dashboard?
Your Netskope Client tunnel has connected to Netskope; however, the user is not receiving any steering or client configuration updates What would cause this issue?
Review the exhibit.
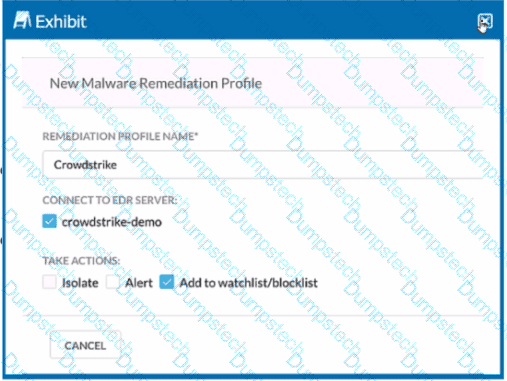
You are asked to integrate Netskope with Crowdstrike EDR. You added the Remediation profile shown in the exhibit.
Which action will this remediation profile take?
You are implementing Netskope Cloud Exchange in your company lo include functionality provided by third-party partners. What would be a reason for using Netskope Cloud Risk Exchange in this scenario?
You built a number of DLP profiles for different sensitive data types. If a file contains any of this sensitive data, you want to take the most restrictive policy action but also create incident details for all matching profiles.
Which statement is correct in this scenario?
A hospital has a patient form that they share with their patients over Gmail. The blank form can be freely shared among anyone. However, if the form has any information filled out. the document is considered confidential.
Which rule type should be used in the DLP profile to match such a document?
You created a Real-time Protection policy that blocks all activities to non-corporate S3 buckets, but determine that the policy is too restrictive. Specifically, users are complaining that normal websites have stopped rendering properly.
How would you solve this problem?
Your company has a large number of medical forms that are allowed to exit the company when they are blank. If the forms contain sensitive data, the forms must not leave any company data centers, managed devices, or approved cloud environments. You want to create DLP rules for these forms.
Which first step should you take to protect these forms?
You are architecting a Netskope steering configuration for devices that are not owned by the organization The users could be either on-premises or off-premises and the architecture requires that traffic destined to the company's instance of Microsoft 365 be steered to Netskope for inspection.
How would you achieve this scenario from a steering perspective?
