Weekend Sale Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = simple70
Pass the CompTIA CySA+ CS0-003 Questions and answers with Dumpstech
An attacker recently gained unauthorized access to a financial institution's database, which contains confidential information. The attacker exfiltrated a large amount of data before being detected and blocked. A security analyst needs to complete a root cause analysis to determine how the attacker was able to gain access. Which of the following should the analyst perform first?
A Chief Information Security Officer (CISO) wants to disable a functionality on a business-critical web application that is vulnerable to RCE in order to maintain the minimum risk level with minimal increased cost.
Which of the following risk treatments best describes what the CISO is looking for?
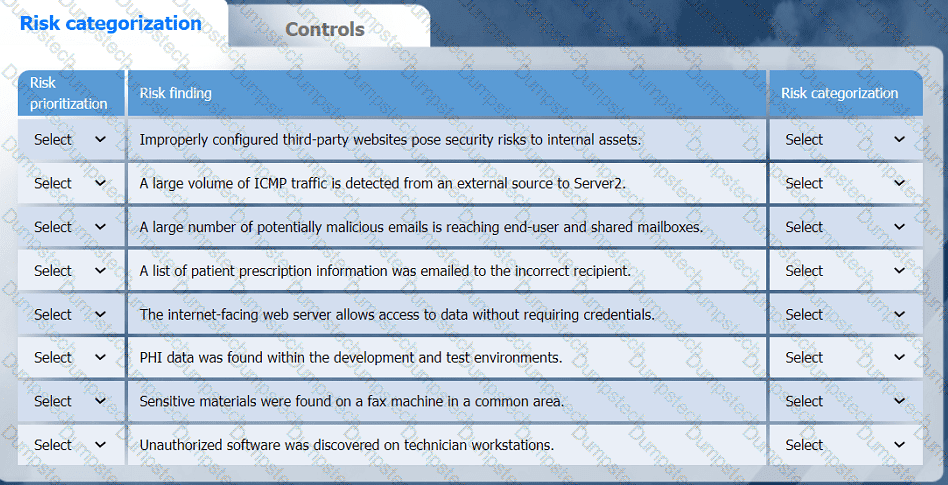
A healthcare organization must develop an action plan based on the findings from a risk
assessment. The action plan must consist of:
· Risk categorization
· Risk prioritization
. Implementation of controls
INSTRUCTIONS
Click on the audit report, risk matrix, and SLA expectations documents to review their
contents.
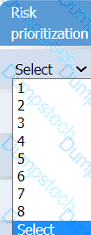
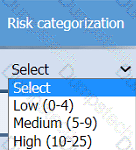
On the Risk categorization tab, determine the order in which the findings must be
prioritized for remediation according to the risk rating score. Then, assign a categorization to each risk.
On the Controls tab, select the appropriate control(s) to implement for each risk finding.
Findings may have more than one control implemented. Some controls may be used
more than once or not at all.
If at any time you would like to bring back the initial state of the simulation, please click
the Reset All button.


Which of the following best describes the process of requiring remediation of a known threat within a given time frame?
A company's internet-facing web application has been compromised several times due to identified design flaws. The company would like to minimize the risk of these incidents from reoccurring and has provided the developers with better security training. However, the company cannot allocate any more internal resources to the issue. Which of the following are the best options to help identify flaws within the system? (Select two).
When starting an investigation, which of the following must be done first?
An incident response team is working with law enforcement to investigate an active web server compromise. The decision has been made to keep the server running and to implement compensating controls for a period of time. The web service must be accessible from the internet via the reverse proxy and must connect to a database server. Which of the following compensating controls will help contain the adversary while meeting the other requirements? (Select two).
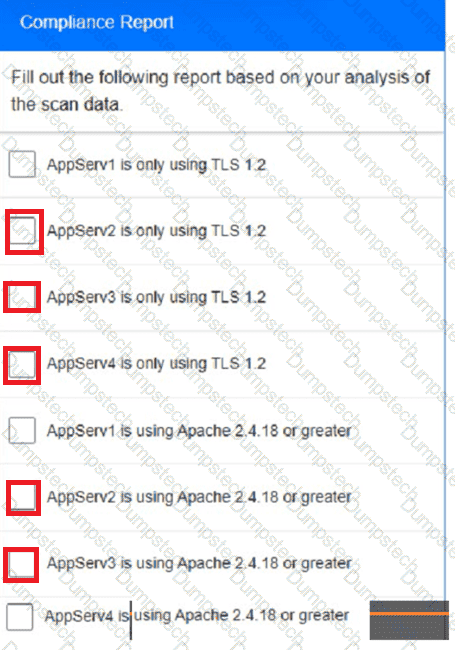
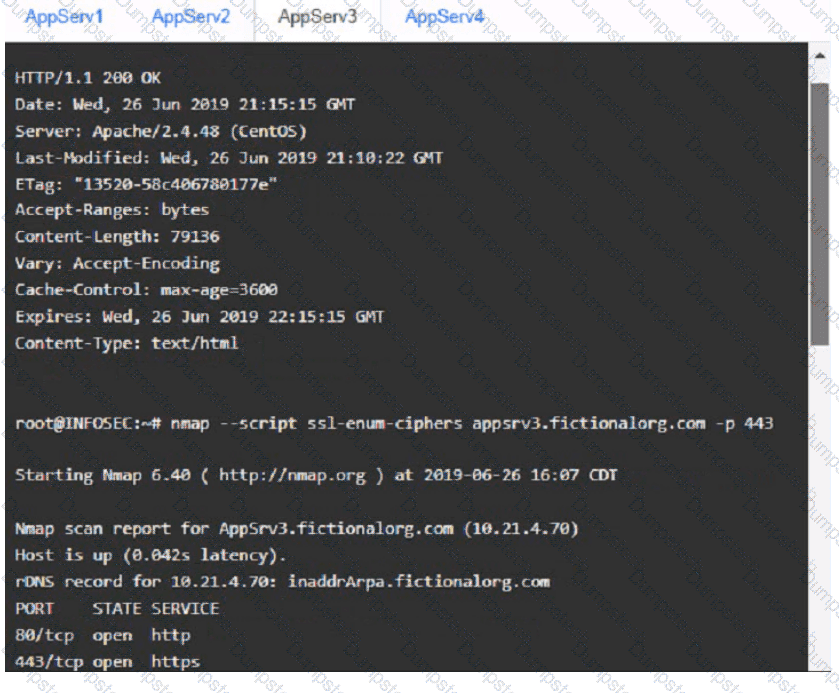
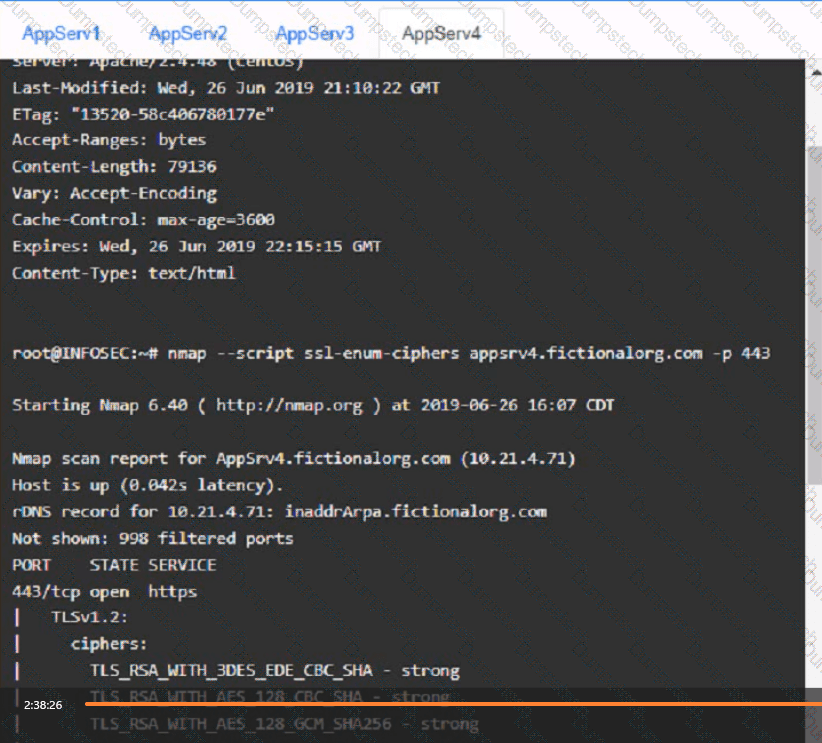
You are a cybersecurity analyst tasked with interpreting scan data from Company As servers You must verify the requirements are being met for all of the servers and recommend changes if you find they are not
The company's hardening guidelines indicate the following
• TLS 1 2 is the only version of TLS
running.
• Apache 2.4.18 or greater should be used.
• Only default ports should be used.
INSTRUCTIONS
using the supplied data. record the status of compliance With the company’s guidelines for each server.
The question contains two parts: make sure you complete Part 1 and Part 2. Make recommendations for Issues based ONLY on the hardening guidelines provided.
Part 1:
AppServ1:
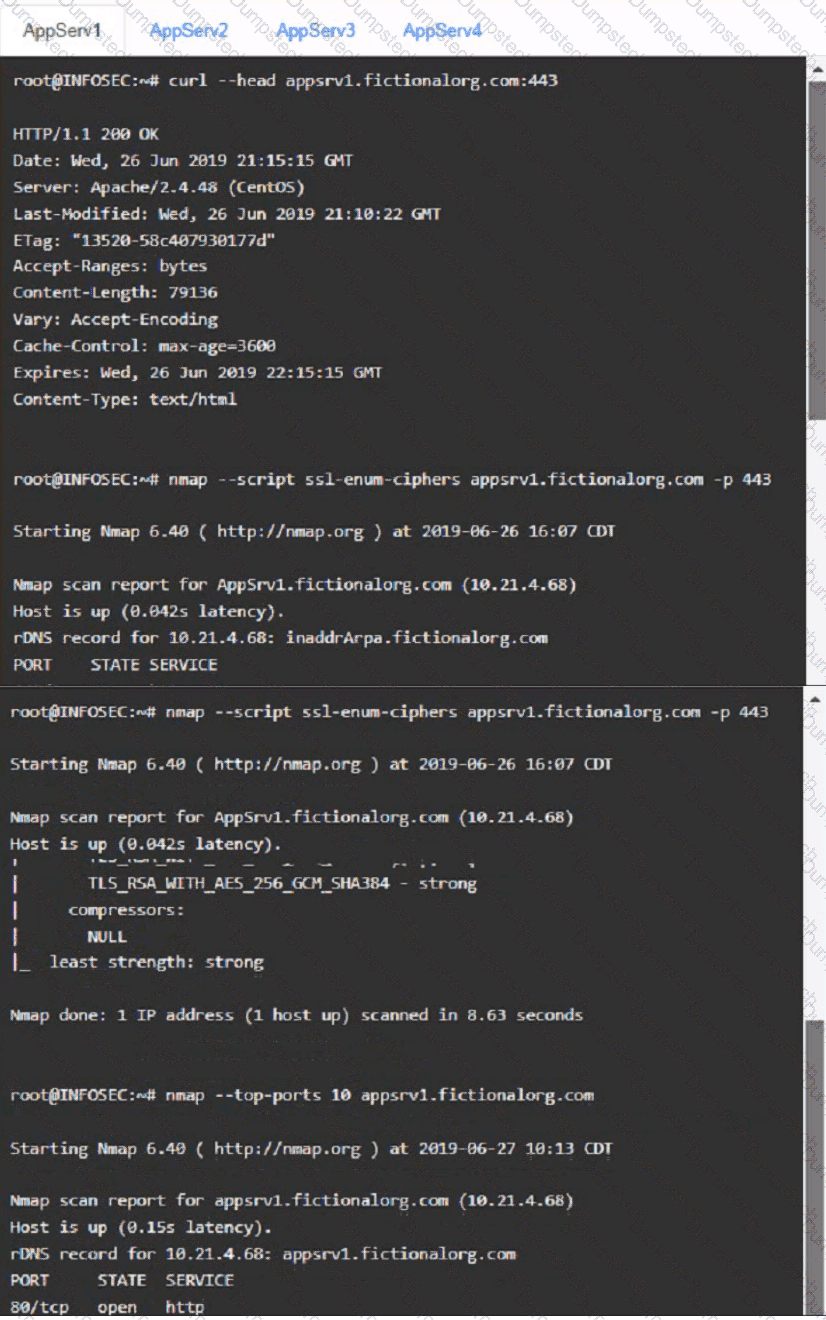
AppServ2:

AppServ3:
AppServ4:
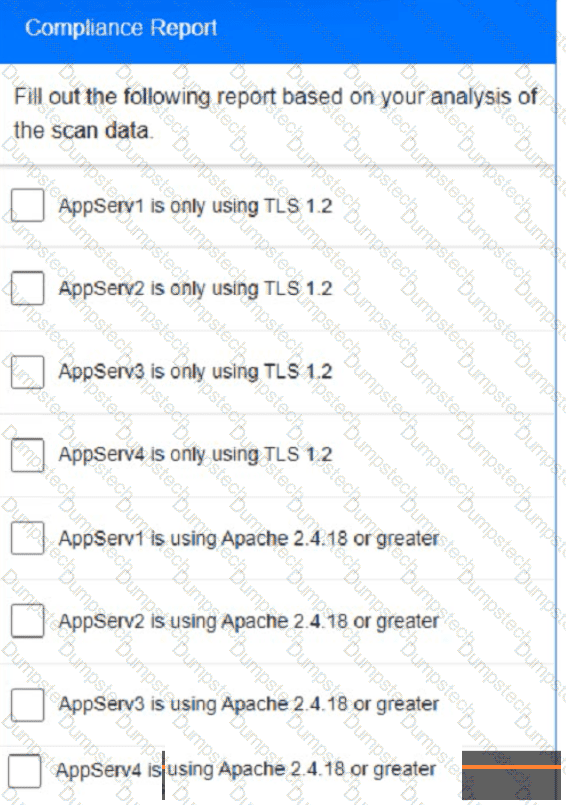
Part 2:
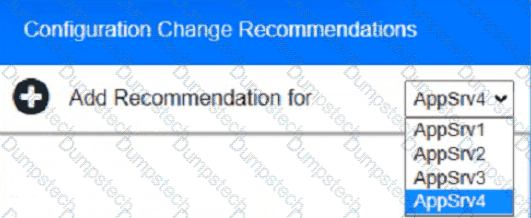
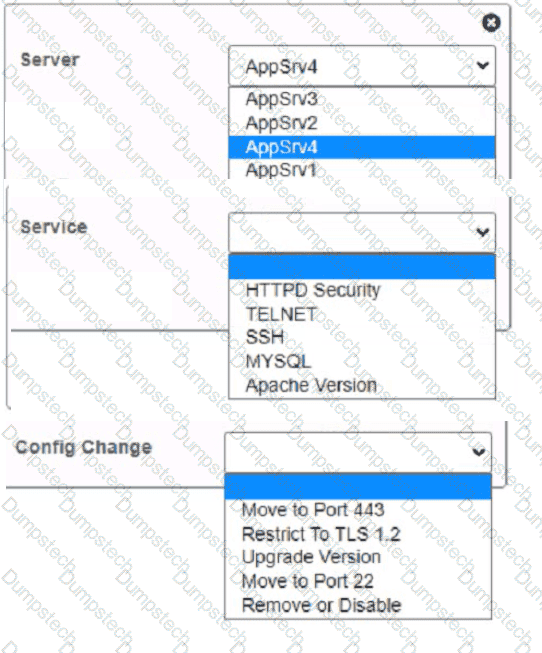
During a training exercise, a security analyst must determine the vulnerabilities to prioritize. The analyst reviews the following vulnerability scan output:
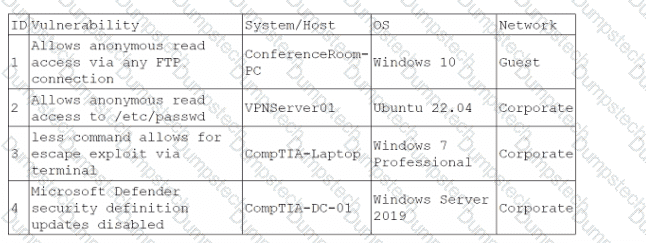
Which of the following issues should the analyst address first?
A company has decided to expose several systems to the internet, The systems are currently available internally only. A security analyst is using a subset of CVSS3.1 exploitability metrics to prioritize the vulnerabilities that would be the most exploitable when the systems are exposed to the internet. The systems and the vulnerabilities are shown below:
Which of the following systems should be prioritized for patching?