CrowdStrike Certification Exams Pack
Everything from Basic, plus:
- Exam Name: CrowdStrike Certified Identity Specialist(CCIS) Exam
- 58 Questions Answers with Explanation Detail
- Total Questions: 58 Q&A's
- Single Choice Questions: 58 Q&A's

Students Passed
Average Score
Questions came word for word
Years Teaching
Explore other related CrowdStrike exams to broaden your certification path. These certifications complement your skills and open new opportunities for career growth.
If you're looking to secure CCIS (IDP) certification, remember there's no royal path to it. It's your prep for this exam that can make the difference. Stay away from those low-quality exam PDFs and unreliable dumps that have no credibility.
To save you from frustration, Dumpstech comes with a comprehensive prep system that is clear, effective, and built to help you succeed without the least chance of failure.
It's overwhelmingly recommended by thousands of Dumpstech's loyal customers as practical, relevant and intuitively crafted to match the candidates' actual exam needs.
Dumpstech's CrowdStrike exam IDP questions are designed to deliver you the essence of the entire syllabus. Each question mirrors the real exam format and comes with an accurate and verified answer. Dumpstech's prep system is not mere cramming; it is crafted to add real information and impart deep conceptual understanding to the exam candidates.
Dumpstech's smart testing engine generates multiple mock tests to develop familiarity with the real exam format and learn thoroughly the most significant from the perspective of CrowdStrike IDP real exam. They also support you to revise the syllabus and enhance your efficiency to answer all exam questions within the time limit.
Dumpstech offers you the most authentic, accurate, and current information that liberates you from the hassle of searching for any other study resource. This comprehensive resource equips you perfectly to develop confidence and clarity to answer exam queries.
Dumpstech's authentic and up-to-date content guarantees you success in the CrowdStrike Certified Identity Specialist(CCIS) Exam certification exam. If you perchance you lose your exam despite your reliance on Dumpstech's exam questions PDF, Dumpstech doesn't leave you alone. You have the option of taking back refund of your money or try a different exam paying no additional amount.
If you want to crack the CrowdStrike Certified Identity Specialist(CCIS) Exam (IDP) exam in one go, your journey starts here. Dumpstech is your real ally that gets you certified fast with the least possibility of losing your chance.
Which menu option isNOTincluded in Falcon Identity Threat Detection (ITD)?
|
D
|
|---|
|
Explanation
Falcon Identity Threat Detection (ITD) providesvisibility, analytics, and detectionof identity-based threats but doesnot include enforcement capabilities. According to the CCIS curriculum, ITD customers have access to investigative and analytical features such asEvent Analysis,Privileged Identities, and relevantSettingsfor visibility and monitoring. Policy Rules, however, are part ofIdentity Threat Protection (ITP)and reside in theEnforcesection of the Falcon console. Policy Rules enable automated responses and enforcement actions, such as blocking access or enforcing MFA, which are not available under ITD-only subscriptions. This distinction is critical in the CCIS material: ITD = Detect and analyze identity threats ITP = Detect + enforce policy actions Because ITD does not include enforcement functionality,Policy Rules are not available, makingOption Dthe correct answer. |
Which of the following areNOTincluded within the three-dot menu on Identity-based Detections?
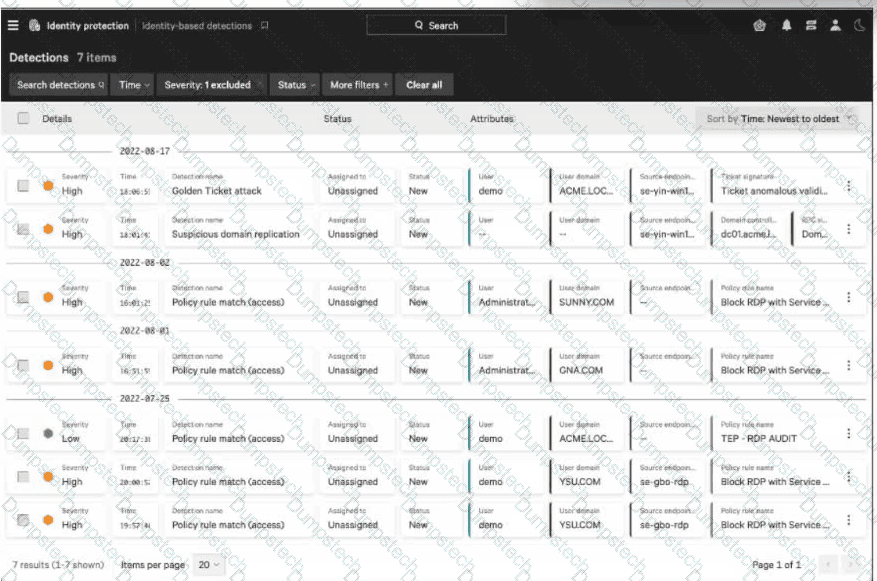
Which of the following are not included within the three-dot menu on Identity-based Detections?
|
B
|
|---|
|
Explanation
In Falcon Identity Protection, thethree-dot (⋮) action menuon anidentity-based detectionprovides analysts with a limited set of actions that applydirectly to the detection itself. According to the CCIS curriculum, these actions are designed to support investigation workflow, tuning, and documentation. The supported actions in the detection-level three-dot menu include: Edit status, which allows analysts to update the detection state (for example, New, In Progress, or Closed). Add comment, which enables collaboration and documentation directly on the detection. Add exclusion, where supported, to suppress future detections that match known benign behavior. Add to Watchlistisnot includedin this menu because watchlists are applied toentities(such as users, service accounts, or endpoints), not to detections. Watchlists are managed from entity views or investigation workflows and are used to increase visibility and monitoring priority for specific identities—not to act on individual detections. This distinction is emphasized in CCIS training to reinforce the separation betweenentity-centric actionsanddetection-centric actions. Because watchlists operate at the entity level,Option Bis the correct and verified answer. |
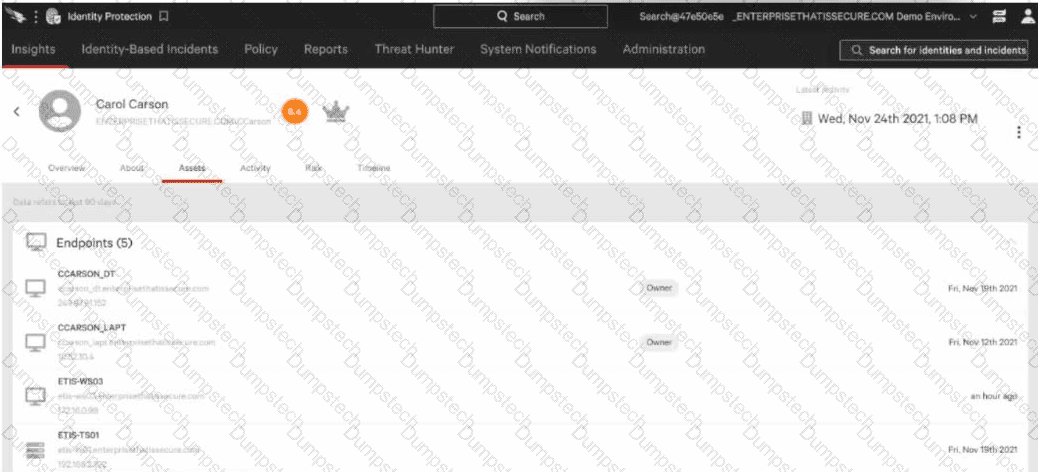
Which of the followingBESTindicates that this user has an established baseline?
|
B
|
|---|
|
Explanation
In Falcon Identity Protection, auser baselineis established by observing consistent and repeatable behavior over time, including authentication patterns, endpoint associations, and usage context. According to the CCIS curriculum, one of the strongest indicators that a user has an established baseline is the presence ofendpoints for which the user is identified as an owner. Endpoint ownership is determined through historical authentication behavior and usage frequency. When Falcon identifies that a user consistently logs into specific endpoints over time, those endpoints are marked asowned, which signifies that sufficient historical data exists to confidently model the user’s normal behavior. This ownership relationship is only created after Falcon has observed the user long enough to establish a reliable baseline. The other options do not definitively indicate a baseline: Logging into multiple endpoints may occur during initial discovery or anomalous activity. A risk score reflects current risk posture, not baseline maturity. Recent logon activity alone does not imply historical consistency. Becauseendpoint ownership requires sustained, predictable behavior over time, it is the clearest indicator that Falcon has successfully established a user baseline. Therefore,Option Bis the correct and verified answer. |
See how DumpsTech helps candidates pass with confidence.
Stay ahead in your career with the latest certification exams from leading vendors. DumpsTech brings you newly released exams with reliable study resources to help you prepare confidently.
Find answers to the most common questions about the CrowdStrike IDP exam, including what it is, how to prepare, and how it can boost your career.
The CrowdStrike IDP certification is a globally-acknowledged credential that is awarded to candidates who pass this certification exam by obtaining the required passing score. This credential attests and validates the candidates' knowledge and hands-on skills in domains covered in the CrowdStrike IDP certification syllabus. The CrowdStrike IDP certified professionals with their verified proficiency and expertise are trusted and welcomed by hiring managers all over the world to perform leading roles in organizations. The success in CrowdStrike IDP certification exam can be ensured only with a combination of clear knowledge on all exam domains and securing the required practical training. Like any other credential, CrowdStrike IDP certification may require periodic renewal to stay current with new innovations in the concerned domains.