Month End Sale Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = simple70
Pass the CrowdStrike CCIS IDP Questions and answers with Dumpstech
Exam IDP Premium Access
View all detail and faqs for the IDP exam
Which menu option isNOTincluded in Falcon Identity Threat Detection (ITD)?
Which of the following areNOTincluded within the three-dot menu on Identity-based Detections?
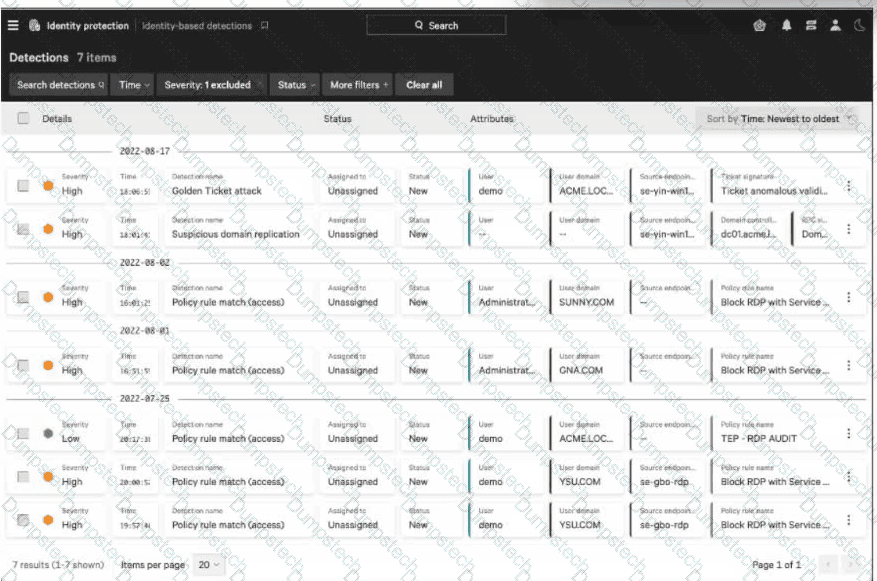
Which of the following are not included within the three-dot menu on Identity-based Detections?
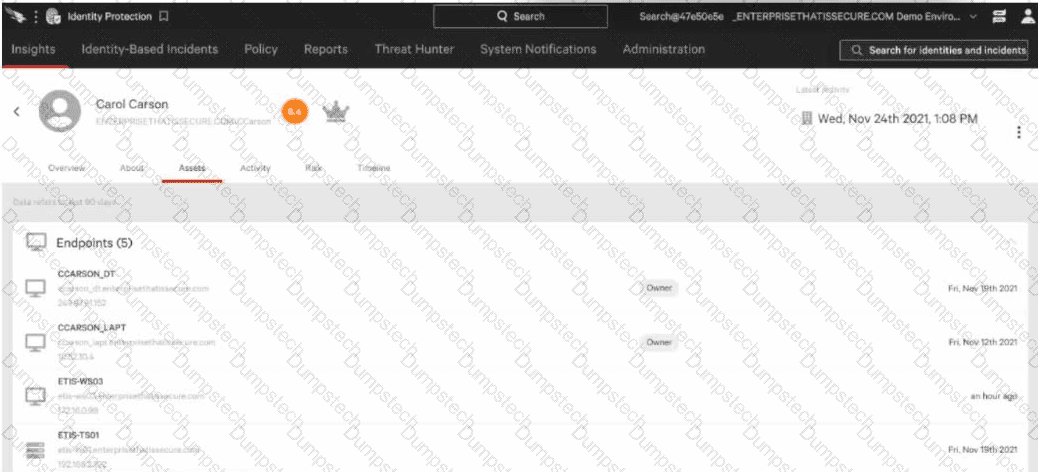
Which of the followingBESTindicates that this user has an established baseline?
Describe the difference between a Human account and a Programmatic account.
Falcon Identity Protection monitors network traffic to build user behavioral profiles to help identify unusual user behavior. How can this be beneficial to create a Falcon Fusion workflow?
Within Domain Security Overview, whatGoalincorporates all risks into one security assessment report?
How should a user be classified if one requires observation for potential risk to the business?
When creating an API client, which scope withWritepermissions must be enabled prior to using Identity Protection API?
Falcon Identity Protection can continuously assess identity events and associate them with potential threatsWITHOUTwhich of the following?
Which of the following best describes how Policy Group and Policy Rule precedence works?
