Spring Sale Limited Time 70% Discount Offer - Ends in 0d 00h 00m 00s - Coupon code = simple70
Pass the PECB ISO 27001 ISO-IEC-27001-Lead-Auditor Questions and answers with Dumpstech
You are performing an ISMS audit at a residential nursing home called ABC that provides healthcare services. You find all nursing home residents wear an electronic wristband for monitoring their location, heartbeat, and blood pressure always. You learned that the electronic wristband automatically uploads all data to the artificial intelligence (AI) cloud server for healthcare monitoring and analysis by healthcare staff.
To verify the scope of ISMS, you interview the management system representative (MSR) who explains that the ISMS scope covers an outsourced data center.
Select three options for the audit evidence you need to find to verify the scope of the ISMS.
You are performing an ISMS audit at a European-based residential
nursing home called ABC that provides healthcare services. You find all
nursing home residents wear an electronic wristband for monitoring
their location, heartbeat, and blood pressure always. You learned that
the electronic wristband automatically uploads all data to the artificial
intelligence (AI) cloud server for healthcare monitoring and analysis by
healthcare staff.
The next step in your audit plan is to verify that the information security
policy and objectives have been established by top management.
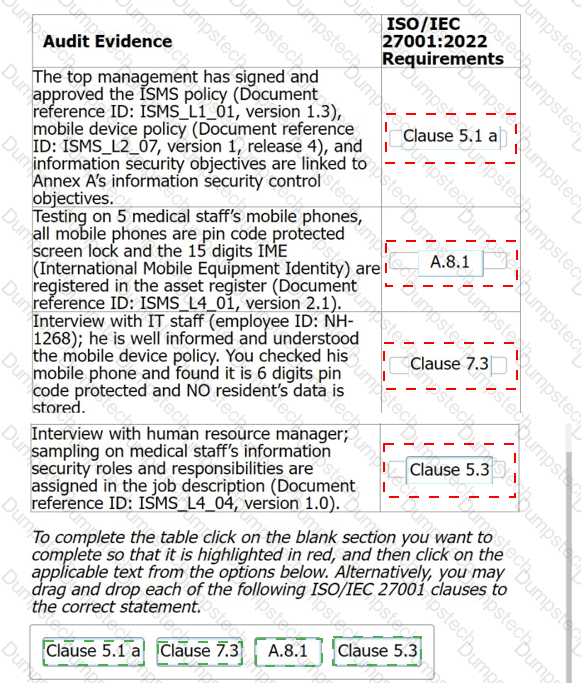
During the audit, you found the following audit evidence.
Match the audit evidence to the corresponding requirement in ISO/IEC 27001:2022.

An organisation is looking for management system initial certification. Please identify the sequence of the activities to be undertaken by the organisation.
To complete the sequence click on the blank section you want to complete so that it is highlighted in red, and then click on the applicable text from the options below. Alternatively, you may drag and drop the options to the appropriate blank section.

You are an experience ISMS audit team leader carrying out a third-party certification audit of an organization specialising in the secure disposal of confidential documents and removable media. Both documents and media are shredded in military grade devices which make it impossible to reconstruct the original.
The audit has gone well and you are just about to start to write the audit report, 30 minutes before the closing meeting. At
this point one of the organization's employees knocks on your door and asks if they can speak to you. They tell you that when things get busy her manager tells her to use a lower grade industrial shredder instead as the organisation has more of these and they operate faster. You were not informed about the existence or use of these machines by the auditee.
Select three options for how you should respond to this information.
Scenario 7
Lawsy is a leading law firm with offices in Bangkok, Thailand. It has over 50 attorneys offering sophisticated legal services to clients in business and commercial law, intellectual property, banking, and financial services. They believe they have a comfortable position in the market thanks to their commitment to implementing information security best practices and remaining up to date with technological developments.
Lawsy has rigorously implemented, evaluated, and conducted internal audits for the information security management system (ISMS) for two years. Now, they have applied for ISO/IEC 27001 certification at ISMA, a well-known and trusted certification body.
During the stage 1 audit, the audit team reviewed all the ISMS documents created during the implementation phase. They also reviewed and evaluated the records from management reviews and internal audits. Lawsy submitted records of evidence that corrective actions on nonconformities were performed when necessary, so the audit team interviewed the internal auditor. The interview validated the adequacy and frequency of the internal audits by providing insight into the internal audit plan and procedures.
The audit team continued verifying strategic documents, including the information security policy and risk evaluation criteria. During the information security policy review, the team noticed inconsistencies between the documented information describing the governance framework and the procedures. Following the completion of stage 1, the audit team leader prepared the audit plan, which addressed the audit objectives, scope, criteria, and procedures.
During the stage 2 audit, the audit team interviewed the information security manager, who drafted the information security policy. He justified the issue identified in stage 1 by stating that Lawsy conducts mandatory information security training and awareness sessions every three months.
Later, the audit team found that Lawsy did not have procedures for using laptops outside the workplace, even though employees were allowed to take laptops outside the workplace. The company only provided general information about the use of laptops and relied on employees’ common knowledge to protect the confidentiality and integrity of information stored on the laptops.
Following the interview, the audit team examined 15 employee training records (out of 50) and concluded that Lawsy meets the requirements of ISO/IEC 27001 related to training and awareness. To support this conclusion, the auditor photocopied and archived the examined employee training records after completing the audit.
Question
During the audit, the team reviewed a sample of training records from 15 out of 50 employees. What does this situation represent? Refer to the scenario.
Question
During an ISO/IEC 27001 certification audit, the audit team leader failed to follow established best practices for conducting the audit. In addition, they lacked the necessary expertise to assess some of the complex areas of the ISMS, leading to suboptimal results. While the audit findings were still reported, some areas of the audit are considered weak and the audit does not fully adhere to the required procedures.
Which level of responsibility does this scenario represent in the case of tortious acts?
Select the words that best complete the sentence:
To complete the sentence with the best word(s), click on the blank section you want to complete so that it is highlighted in red, and then click on the applicable text from the options below. Alternatively, you may drag and drop the option to the appropriate blank section.
You are carrying out your first third-party ISMS surveillance audit as an audit team leader. You are presently in the auditee's data centre with another member of your audit team and the organisation's guide.
You request access to a locked room protected by a combination lock and iris scanner. The room contains several rows of uninterruptable power supplies along with several data cabinets containing client-supplied
equipment, predominantly servers, and switches.
You note that there is a gas-based fire extinguishing system in place. A label indicates that the system requires testing every 6 months however the most recent test recorded on the label was carried out by the
manufacturer 12 months ago.
Based on the scenario above which two of the following actions would you now take?
Question:
EquiBank is undergoing an external audit of its financial management system. The auditors evaluate the logic of transactions processed by EquiBank's financial software. To ensure accuracy, they use simulations to validate operations, calculations, and controls programmed in the software applications. What type of Computer-Assisted Audit Technique (CAAT) is used?
You are an experienced audit team leader conducting a third-party surveillance audit of an organisation that designs websites for its clients. You are currently reviewing the organisation's Statement of Applicability.
Based on the requirements of ISO/IEC 27001, which two of the following observations about the Statement of Applicability are false?